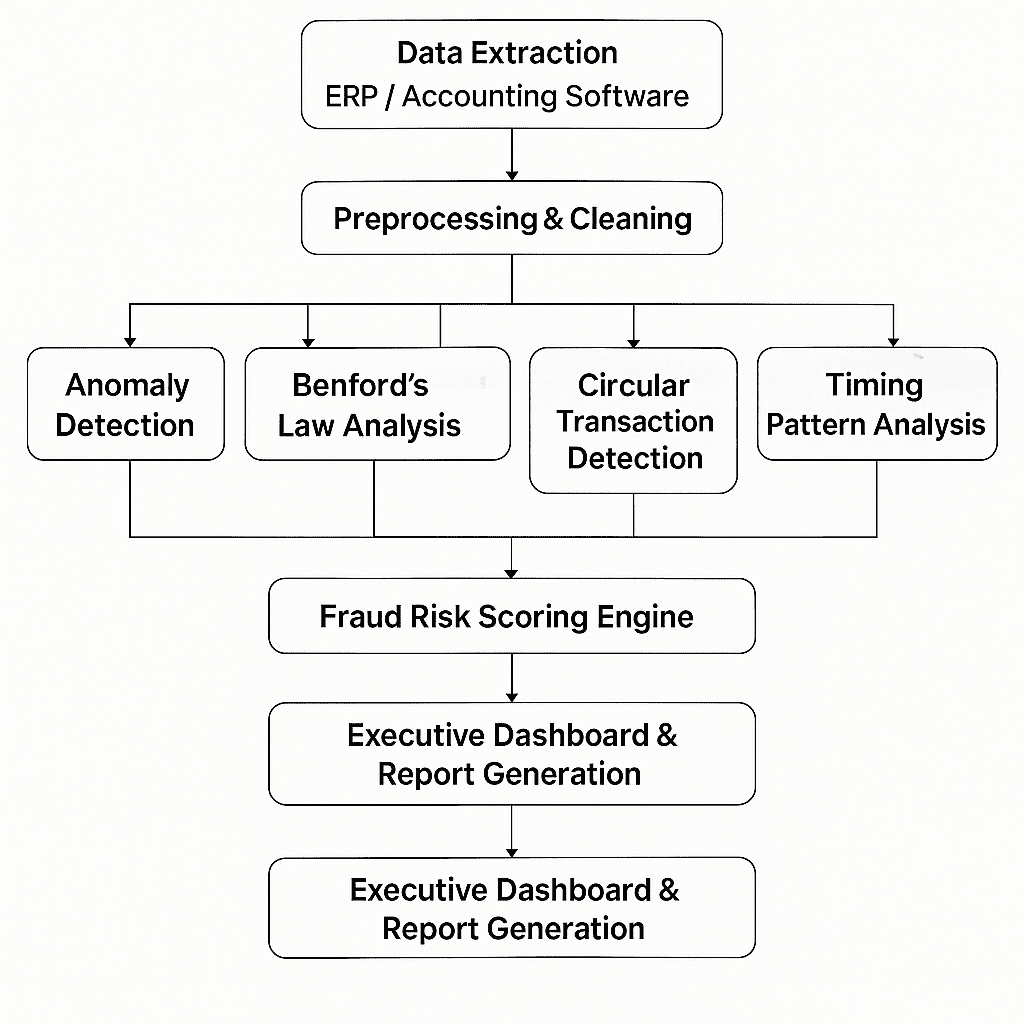
💻 What is a Cyber Attack?
A cyber attack is an intentional attempt by hackers or malicious actors to access, disrupt, or damage computer systems, networks, or data. These attacks can target personal devices, corporate networks, or critical infrastructure — often leading to financial loss, reputational damage, and legal consequences.
| Attack Type | Description |
|---|---|
| Phishing | Deceptive emails or messages tricking users into revealing sensitive info. |
| Ransomware | Malware that locks/encrypts data and demands a ransom to restore access. |
| Denial of Service | Overwhelms a server with traffic, causing it to become unavailable. |
| Man-in-the-Middle | Intercepts communication to steal or manipulate transmitted data. |
| SQL Injection | Malicious code injected into a web app to access or manipulate databases. |
| Zero-Day Exploit | Targets unpatched vulnerabilities before developers release a fix. |
| Credential Stuffing | Uses leaked username/password combos to access user accounts. |
| Spyware | Secretly monitors user activity and collects information without consent. |
🔍 Notable Cyber Attacks in Recent Years
WannaCry (2017) – A global ransomware attack that affected over 200,000 computers in 150 countries.
SolarWinds Hack (2020) – A sophisticated supply chain attack targeting U.S. federal agencies and private companies.
Colonial Pipeline Attack (2021) – A ransomware attack that disrupted fuel supply across the Eastern United States.
These incidents underscore how even large, well-funded organizations are vulnerable to cyber threats.
- Cyber Attack Trends in 2024–25
Rise in AI-powered phishing and deepfake scams.
| Attack Type | Description |
|---|---|
| Phishing | Deceptive emails or messages tricking users into revealing sensitive info. |
| Ransomware | Malware that locks/encrypts data and demands a ransom to restore access. |
| Denial of Service | Overwhelms a server with traffic, causing it to become unavailable. |
| Man-in-the-Middle | Intercepts communication to steal or manipulate transmitted data. |
| SQL Injection | Malicious code injected into a web app to access or manipulate databases. |
| Zero-Day Exploit | Targets unpatched vulnerabilities before developers release a fix. |
| Credential Stuffing | Uses leaked username/password combos to access user accounts. |
| Spyware | Secretly monitors user activity and collects information without consent. |
📜 Legal & Compliance Perspective
Cybersecurity is no longer optional — it's a legal obligation. In India, businesses must comply with:
👨💼 How Sompalli & Co Can Help
At Sompalli & Co, we offer end-to-end cyber risk advisory services, including:
Our team of experts helps you build a resilient digital ecosystem, backed by compliance and governance.
Conclusion
Cyber attacks are an ever-growing threat in the digital age, but with the right awareness, tools, and strategy, they can be prevented or minimized. Proactive cybersecurity is not just an IT responsibility — it’s a business imperative.